Stealer Malware Logs
2024-04-05
Over the last few months, WhiteBlueOcean cyber analysts have observed a significant rise in the sharing of so-called stealer log files across dark-web forums, messaging services, and other platforms monitored by WhiteBlueOcean. In this article we will dive into what stealer logs are, the risks that they pose to consumers, and what can be done to help protect you from this risk vector.
What are stealers?
Stealers, as a term, refers to a 'family' of malware that is used to steal log in credentials from users. These can take many forms, such as keyloggers, and have different attack vectors.
Depending on the kind of stealer, it may:
log a user’s keystrokes and send them back to a bad actor, who will be able to search the logs for user/email and password combinations;
access saved passwords within browser files;
create man-in-the-middle attacks to steal login credentials.
The infection vectors vary, but some common ways avenues include:
Compromised email attachments;
Malvertising (malicious code injected into advertisements online, which can infect a victim when they click on it);
Downloading and using cracked software (pirated software that has been modified to remove copy protection) which may have malware hidden within the files;
Visiting illegitimate websites (such as unlicensed streaming platforms) that may infect the user.
What are stealer logs, and why are they being shared?
Stealer logs, as the name might suggest, are the logged data collected by stealer malware. Whilst there can be a lot of variety in the kinds of data stolen and how it is presented (due to the multiple types of stealer being used by bad actors), there are two dominant types of log that WhiteBlueOcean have been running across.
Unparsed logs:
These are the logs presented in their rawest form, often shared in large batches containing the data of hundreds (if not thousands) of victimised devices. Each device will provide various sets of data which is loosely categorised into categories such as user credentials stored by a web browser, information about the device, credit card information and cryptocurrency wallet addresses. By combing through this data and combining the various elements within each log a bad actor could build up a fairly comprehensive set of information on each victim, which they might then use to carry out account takeovers, syphon funds (either fiat currency or cryptocurrency), or carry out identity fraud; alternatively, they may simply sell or trade such information.
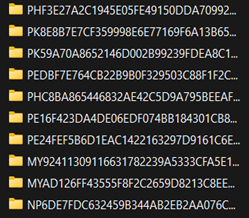
1. Sample of folders shared as unparsed logs
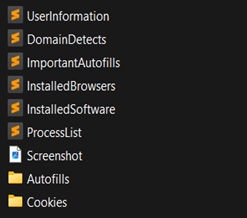
2. Sample of files shared within a folder from unparsed logs
Parsed logs:
Unlike the unparsed logs mentioned above, parsed log files are presented as long lists (often containing millions of records) of credentials (such as a username, phone number or email address, along with a password), in a very similar fashion to combolists. Unlike combolists (which are often used in credential-stuffing attacks where a bad actor attempts to gain access to a service by trying numerous credential sets in the hope that one may grant access), these parsed logs carry one more salient piece of information: the URL of the service relating to those credentials. This results in a significantly higher risk as a bad actor knows where these log-in credentials were used, and thus can be much more targeted in their nefarious activities.
Why are these being shared?
Whilst historically WhiteBlueOcean analysts have seen such data being sold, or offered in exchange for other data, the status quo is that these large sets of data are being shared for free. This leads us to ask the very straightforward question: why? The answer, perhaps surprising to some given that we have looked at the potential value of this data to bad actors, is advertising. What exactly is being advertised? The answer to that is two-fold. In some cases, it is very simply a case of a bad actor advertising data for sale – saying “See what I am offering for free, imagine the quality of the data that you could purchase from me!” In the other case, which is growing more and more prevalent, they may be advertising Malware-as-a-Service (which we will refer to as MaaS from now one). MaaS is a concept very similar to Software-as-a-Service (a concept very commonly used in the modern business world) whereby a bad actor will offer access to a tool (in this case stealer malware, but other options, such as ransomware, are also distributed on a similar model), either for a one-off fee or as a subscription model (or as percentage of any proceeds of crime, although this does usually relate to stealers on a MaaS model). This development in the world of cyber-criminals significantly lowers the barriers to entry, as bad actors do not necessarily need the technical know-how that they once would have; they can now simply pay for the tool and the instructions on using it.
How to mitigate the risks?
Whilst it may feel that we are constantly being informed about new risks, and how overwhelmed that might make us feel, there are some steps we can take to reduce the risk of being infected with stealers (a lot of which should feel familiar to those who already carry out good cyber-security practices):
- Keep your antivirus software up to date, and run regular scans on your devices
- Avoid using pirated software as these can come with the added bonus of malware
- Be vigilant about opening email attachments, especially if they are not expected
- Utilise multi-factor authentication when the option is available to you, as this adds a barrier to any bad actor who may have access to your credentials
- Avoid visiting questionable websites or clicking on adverts that seem too good to be true
- Maintain good password hygiene; avoid using the same password across multiple services and regularly update your passwords (a good password manager can help with this)
Finally, if you are informed that your credentials have been found within stealer logs it is very important to act swiftly (update your passwords and run thorough virus scans, and remain vigilant for strange activity on your accounts)
The information contained in this article is provided for informational purposes only and does not constitute professional advice and is not guaranteed to be accurate, complete, reliable, current or error-free.

Related news

Hackers Are Using CAPTCHA as Attack Vector
2025-03-14Cybercriminals use malicious CHAPTCHAs to install stealers on victims' computers, collecting sensitive data such as emails, passwords, addresses, and financial information. We examine various attack methods, including watering hole attacks, ad abuse, and SEO poisoning, and provide practical tips for protecting yourself from these sophisticated threats.
Read more
Antivirus Evasion: Why Cyber Attacks Still Succeed
2025-06-20Cybercriminals are mastering antivirus evasion, using tactics like code obfuscation, encryption, and process injection. Real-world breaches show why antivirus alone isn’t enough—and how layered protection like EDR is essential to securing your data.
Read more
AI tools – Is it time to let it go?
2025-05-21AI tools have become essential in daily life, but their rise also brings significant cybersecurity threats. From malicious downloads to data breaches, this article explores the risks and offers tips on staying safe in the age of AI. Learn about the importance of trusted sources, 2FA, and cybersecurity awareness.
Read more
The shift to private clouds: how cybercriminals are changing the monetization of stolen data
2024-11-22Subscription-based models in cybercrime allow hackers to offer stolen data in private clouds, reducing risks and boosting profits. For victims, this means greater threats as data becomes more accessible and exploitable over time.
Read more
When hacking is good: ethical hackers
2022-06-06While talking about the ethics of hackers, the term hacker often has a negative connotation. In reality, a hacker is an extremely competent person in the IT sector who exploits his knowledge, skills and his own curiosity for helping others in order to discover the vulnerabilities of a system.
Read moreContacts
Let's talk
Please fill in the form below (fields with * are mandatory) and we will respond to your request as soon as possible!