Telegram and the Shifting Landscape of Cybercrime
2025-11-11
Telegram, once known as a free speech haven and a safe space for all things criminal and not, has found itself at the centre of a dramatic shift in the cybercriminal underworld. Known for its encrypted messaging and minimal moderation, the platform has long been a favourite among bad actors who used it to communicate, plot attacks and share and sell stolen data. But recent policy changes have disrupted this well-established process, forcing cybercriminals to adapt to new rules and look for new spaces to carry out their work.
Telegram’s Dual Identity
Telegram’s rise to prominence has been marked by its dual identity. On one hand, it is a legitimate communication app used by millions for everyday messaging, news, and community building, especially on the Russian-speaking side of the world. On the other, it has become a hub for illegal activity, hosting everything from stolen data marketplaces to ransomware communication channels.
It comes as no surprise that cybercriminals are drawn to Telegram. Its features include end-to-end encryption, the possibility of using anonymous usernames, a lack of centralized moderation and options to create groups and channels, both public and accessible only to approved members. Unlike traditional dark web forums and websites, Telegram is easy to access and doesn’t require special software like Tor browser. This accessibility has made it a go-to platform for both seasoned hackers with years of experience and beginner criminals.
The Policy Shift
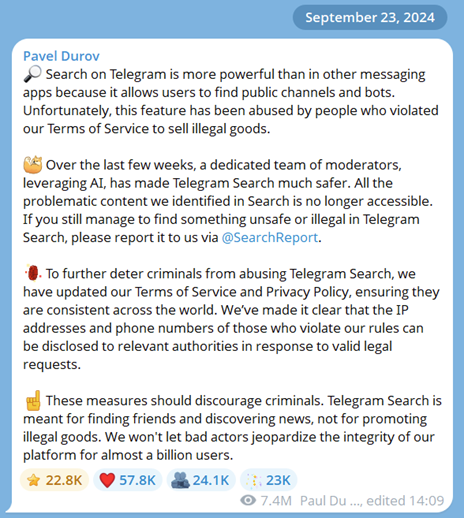
In mid-2025, Telegram announced a significant policy update that turned the dark side of Telegram upside down. Following the arrest of Telegram CEO Pavel Durov in Paris in August 2024 for insufficient moderation of illegal activities on the platform, Telegram announced it would begin cooperating with law enforcement. This included sharing user information, such as IP addresses and phone numbers, of users who are suspected of criminal activity with relevant authorities upon request. This came as a surprise to many Telegram users, considering the platform was well-known to prioritise user privacy.
The message shared on Pavel Durov’s account highlighted that the changes were only limited to a certain type of content and users and were aimed to make the platform a safer space. The response to the update, however, was not entirely enthusiastic.
The Immediate Fallout
The reaction from the cybercriminal community was swift and chaotic. Within days, numerous high-profile criminal groups and channels vanished. Admins deleted groups, scrubbed content, and issued warnings to followers. Some users reported sudden account bans, while others claimed their messages were being monitored. More and more groups appeared as ‘can’t be displayed’ or disappeared without a trace. Even the backup channels and the backups of backups seemed to go.

For a while, one of the main topics of discussion on dedicated dark web forums was Telegram’s “betrayal”. Many speculated that the platform had already begun handing over user data, citing unexplained group shutdowns and increased scrutiny. The sense of paranoia was undeniable.
Migration
As Telegram tightened its policies, cybercriminals began migrating to other platforms. Some turned to decentralized messaging apps that do not have a central server or authority and offer end-to-end encryption like Tox, Session, and Element. Many moved to Signal - a privacy-focused messaging app and website that does not store metadata and uses disappearing messages feature. Others reverted to old-school methods like IRC channels, encrypted email, or dark web forums.
Interestingly, not all bad actors fully abandoned Telegram. Some adapted by changing their tactics - using coded language, creating private invite-only channels, and using multi-layered selection processes to avoid detection. Many cybercriminals create multiple backup groups that users are invited to join to avoid disruption if one was to be suddenly removed. The goal was to continue operations while staying under the radar.
This sudden spread of criminals who used to all reside in the same space has made it harder for cybersecurity professionals to track threats. Telegram’s public channels were relatively easy to find and monitor, but newer platforms are more obscure and complex and the users are more careful.
Implications for Cybersecurity Professionals
For cybersecurity teams, Telegram’s policy shift is both a blessing and a challenge. On one hand, it has disrupted several major cybercrime operations, reducing the visibility and reach of threat actors. On the other hand, it has resulted in scattering of bad actors into online spaces that are harder to track, monitor and disrupt. Threat intelligence teams now face the hard task of exploring and mapping out these new digital territories. This includes developing new tools to monitor decentralized platforms, analysing encrypted traffic, and collaborating with law enforcement across jurisdictions.
What now?
Looking ahead, the dark industry will most likely continue to adapt. Cybercriminals are smart and resourceful, and history has shown that crackdowns often lead to new ideas and developments. We may see the rise of new platforms designed specifically to evade detection, or the resurgence of older methods like peer-to-peer networks and encrypted forums. What is almost a given is that radical policy shifts are not the end of cybercrime but just a temporary inconvenience.
As a result, law enforcement and cybersecurity teams will need to stay alert. This includes investing in threat intelligence, building cross-platform monitoring capabilities, and fostering international cooperation. It is more important than ever to keep a close eye on what those groups and people will do next.
Conclusion
Telegram’s shift from a digital sanctuary for free speech and illegal activity into a more regulated platform marks a pivotal moment in the evolution of the dark industry. While its enforcement has disrupted familiar patterns of cybercriminal operations, it has also caused bad actors to scatter to spaces and platforms that aren’t as easy to detect and monitor.
In the end, Telegram’s policy change is not a final resolution but a redirection. It is clear that cybercrime is not disappearing. It is constantly changing. Evolving. With new laws and policies inspiring new solutions. The question threat intelligence teams have to answer now is not only when the currently silent groups will reappear but where and in what form.
Sources
https://www.ibm.com/think/insights/what-telegrams-recent-policy-shift-means-for-cyber-crime
The information contained in this article is provided for informational purposes only and does not constitute professional advice and is not guaranteed to be accurate, complete, reliable, current or error-free.
Related news

ToolShell and SharePoint: A Hackathon Gone Wrong
2025-09-25This article summarizes the timeline of the ToolShell exploit, a Microsoft SharePoint zero-day vulnerability. It covers the exploit's rapid spread, which affected critical US government departments, and highlights how slow patching contributed to the attacks.
Read more
Is Microsoft Teams Secure? A Look at Emerging Threats
2025-08-22Trusted by millions of people, Microsoft Teams is now a playground for cybercriminals. This article explores social engineering tactics, real malware campaigns like DarkGate, and offers practical steps to stay safe in today’s evolving threat landscape.
Read more
The Great Cybercriminal Migration: Why Stolen Data Went Private in 2025 and What to Expect in 2026
2025-12-05Following a massive takedown of data leak sites in 2025, the cybercrime landscape appears to have visibly shrunk. But has it really? Though less stolen data appears on the surface, the vast majority of bad actors have simply slipped underground, continuing to operate quietly.
Read more
Antivirus Evasion: Why Cyber Attacks Still Succeed
2025-06-20Cybercriminals are mastering antivirus evasion, using tactics like code obfuscation, encryption, and process injection. Real-world breaches show why antivirus alone isn’t enough—and how layered protection like EDR is essential to securing your data.
Read more
Akira: the ransomware group quietly building a cybercrime enterprise
2025-06-04Akira has quickly become one of the most feared ransomware groups that emerged in 2023, launching indiscriminate attacks across countries and sectors. Known for its aggression, use of double extortion, and links to Conti and Ryuk, Akira represents a new level of cybercrime professionalism and global risk.
Read moreContacts
Let's talk
Please fill in the form below (fields with * are mandatory) and we will respond to your request as soon as possible!