Could You Be the Target of Cyber Crime?
2023-10-02
Bad actors, who may be any kind of hacker, carder, social engineer or otherwise, are always on the hunt for their next victim. These are opportunistic criminals who, at risk of their own imprisonment, will prey on ordinary people in order to gain access to their accounts and financial credentials. They may try to blackmail you, extort you, sell your data on to other criminals, or exfiltrate funds from your accounts themselves. But how likely is it that you, yourself, are attacked in this way? Are you a target?
In this article we will take a look at some of the popular techniques employed by bad actors, and who exactly is at risk of these techniques - be it high office business executives, or your average everyday person.
Technique 1: Credential Reuse
If you have been on the internet for a while, it is very likely that your information has already fallen into the hands of criminals before. You may even have been hacked in the past, or been unfortunate to find yourself the victim of identity theft or fraud. Unfortunately, many businesses that we have previously entrusted with our information, including emails, passwords, card details and personal information, have mishandled our data. By not taking stronger precautions against cybercrime, they have themselves fallen victim to attacks and the data that we provided them has been leaked.
White Blue Ocean leads the market in dark web monitoring. In 2022, our yearly review of the data that is distributed online shows that 90.5% of all email addresses also have a password attached, with the vast majority of this data being passed around between criminals on the dark web. These email-password combinations come from a multitude of sources, such as phishing, malware, and data breaches that could be anywhere up to 20 years old, however even today that information can be used by bad actors to brute-force access to your online accounts.
When it comes to email-password combinations specifically, these are exchanged on the dark web in the form of lists that can range from hundreds of lines, to hundreds of millions. For bad actors, it is a simple matter of testing each email and password on a multitude of different websites in order to check if any work. This is why we at White Blue Ocean will always advocate for the regular changing of your password, the establishing of multi-factor authentication and the use on unique passwords on each website that you use.
Who are the targets of this type of attack?
Since the origins of this data can vary broadly, these attacks can appear indiscriminate. A bad actor using such a list might pay little regard to the individual whose account they are trying to access, and is merely hoping to gain access to any of them. However, these lists are not always such a mixed bag.
Bad actors will often organise these lists by country, or by email extension. Therefore, you may be at greater risk if a bad actor decides to target specifically European or North American countries, for example. The exchange of email credentials likely mirrors trends seen in the exchange of card information, in which the United States, the United Kingdom and Russia all occupy the top spots for countries most affected.
However, these lists can also be put together as the result of specific corporate data breaches. This means that if a company has suffered a breach in the past, these credentials could be used to target that company specifically. Further to this, if any information about the company's staff is available online, such as through Facebook or LinkedIn, individual staff members may find themselves much more at risk due to their position in the company.
In conclusion, the likely victims of this type of brute-force attack can vary broadly, but especially are those who have been affected by data breaches in the past.
Technique 2: Phishing
Phishing is a technique employed by bad actors which manifests in a variety of different ways. The most common form of phishing, and the one which people are most familiar with, is email spam. This is where bad actors will send emails en masse to millions of individuals at a time, all of which might include a malicious attachment, or a fraudulent hyperlink. The aim of these emails is to trick you into divulging your information to the sender, so they will often disguise themselves as respectable bodies such as banks, national organisations or other large companies. This kind of phishing can also be done via text message, by post, or by phone.
Where do bad actors get your email from? These again can be obtained from the lists described above, however in addition to these lists, some companies of ill repute may opt to sell your email address. Active email addresses are valuable to bad actors, as many of the emails from the aforementioned lists may be inactive, so some criminals will pay for access to a high quality mailing list to bombard with phishing emails. To mitigate this, you may find it beneficial to sign up for websites with a throwaway email account, or to use an email obfuscation service which is provided by some of the larger email providers.
This technique may appear relatively indiscriminate, but it can be adapted to be far more effective against select individuals. This is termed spear phishing.
Segment: Spear Phishing
The way spear phishing differs from other forms of phishing is that the attacks are far more discriminatory towards specific individuals or small groups. Because of this narrowing of the scope of this attack, bad actors are able to massively increase the sophistication of these attacks which in turn makes them far more effective. This can include highly accurate impersonations of other individuals such as company staff, expansive knowledge on the operations of a business, fake emails, social media profiles, websites and so on, all engineered very specifically to fool a small handful of individuals.
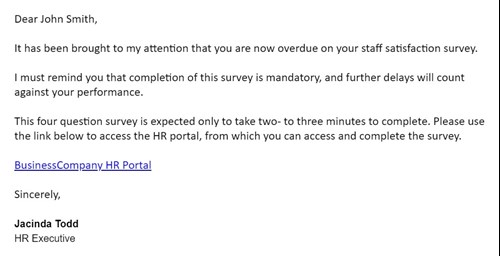
To give an example: you receive an urgent email from human resources saying that your staff satisfaction survey is overdue, and that it may be marked against your performance if not completed immediately. You think it harmless enough, so you click the link provided which brings you to a page that looks exactly like your company's human resources portal. You are asked to enter your email and password, which you proceed to do, however it informs you that you entered incorrect information. You try a couple more times, a few different passwords, however cannot gain access.
You may not have noticed that, although you were familiar with the name of the human resources staff that sent you the email, that it was not from their usual email address. And further, the link that they provided you did not actually direct you to your company's website, but an exact copy of it. Every time you tried to log in, each email and password combination was sent to a bad actor who can now access your workstation and gain access to your company's network.
 |
|
Figure 1: An example fake internal email which uses hyperlinked text to obfuscate a fraudulent external link. |
With access to your company's network, bad actors can infect systems with ransomware and other malware, or extract critical business information to extort your company with. Suffice to say that, even from interacting with what appeared to be a relatively harmless email, the consequences can be extreme.
Who are the targets of this type of attack?
Similarly to the brute-forcing of accounts with reused credentials, the perpetrators of phishing attacks can apply their techniques very indiscriminately. However, when it comes to spear phishing, these attacks can be highly sophisticated such that even trained professionals can fall victim to them.
You are most at risk of spear phishing if you occupy a senior position in your company, or are otherwise expected to have wider systems access such as an IT or security professional. If this describes your current employment, then you must take extra precautions when opening attachments, accessing external links, and even answering the phone. There have been cases where AI has been used to mimic somebody's writing style, and even impersonate their voice in real time during phonecalls. Therefore, it is important to check, double check and triple check the authenticity of each and every contact.
Education matters
Bad actors have a number of techniques which they can employ to gain access to sensitive information, and we have covered but two of them. However, these two techniques illustrate well how bad actors can fine-tune their approaches to indiscriminately target a large group of people, or to launch dangerous and highly sophisticated phishing campaigns against individuals and small groups of people at a time.
As a business, it is your responsibility to ensure the continued vigilance and education of your staff on security matters, and as an individual it is your responsibility to safeguard your company's and your own information from cyber criminals.
Sources
https://www.whiteblueocean.com/glossary/
https://www.whiteblueocean.com/newsroom/crif-cyber-observatory-2022-yearly-report/
https://every.to/chain-of-thought/how-to-make-ai-write-like-your-favorite-author
https://www.cbsnews.com/news/artificial-intelligence-phone-scam-fake-voice/
The information contained in this article is provided for informational purposes only and does not constitute professional advice and is not guaranteed to be accurate, complete, reliable, current or error-free
Related news

The role of Initial Access Brokers
2022-08-01In the cybercriminal business model, initial access brokers have become a crucial figure, acting as middle-men between attackers and victims, by providing the attackers with access methods to enter victims’ networks.
Read more
The dangers of VPN credential leaks
2022-07-22The increased reliance on VPNs made the latter an attractive target to cybercriminals. In particular, threat actors began exploiting one of the known weakest links in the chain: users’ passwords.
Read more
The Power of Data: How Stolen or Compromised Credentials From Employees Can Harm a Business
2024-08-02While a set of login credentials stolen from a personal account can cause a big inconvenience for an individual in the form of identity theft and financial loss, the same set of credentials taken from an employee’s company account can cause much larger-scale disruptions and financial losses to the company and its customers, as well as putting other employees and customers at risk. In this case, a simple password change might not cut it.
Read more
Twitter data breach: exposed the data of 5.4 million accounts
2022-09-15In late July 2022, Twitter confirmed that it had suffered a data breach, after a threat actor appeared in a popular underground forum selling the data of 5.4 million Twitter users. Read more
Read more
How Bad Actors Begin
2023-08-02There is a clear path of progression for a bad actor to go from unknown and uninvolved, to standing shoulder to shoulder with the internet's most sophisticated criminals. In this article we attempt to answer the question of how bad actors are made.
Read more
SIAE Data Breach
2021-10-21News of the latest cyberattack comes from Italy, where on the afternoon of the 20th October it was disclosed that SIAE, the Italian Society of Authors and Publishers, was targeted by a ransomware attack. SIAE, which was founded in 1882, is the Italian copyright collecting agency for artists in different areas of the entertainment industry, including television, music, theatre, visual arts and literature, and aims to guarantee that artists receive the right remuneration for their work.
Read more
Why phishing emails contain errors?
2022-05-04You have probably noticed that all the phishing mails are poorly written and some details may let us think they are somewhat unprofessional. Find out why.
Read moreContacts
Let's talk
Please fill in the form below (fields with * are mandatory) and we will respond to your request as soon as possible!