Why phishing emails contain errors?
2022-05-04
Phishing poses a serious threat to both individuals and companies.
The phishing statistics give an idea of the prevalence and severity of phishing attacks, which are mainly carried through email phishing as primary vector (96%1 according to “IBM's 2021 Cost of a Data Breach Report.
The objective of a phishing attack is to steal credentials to victims or steal personal information, thus the hacker can perform any type of fraud.
Whilst phishing can take many forms and the bad actor can request various types of information to the target, all emails and communication share some characteristic.
You have probably noticed that, all the phishing mails are poorly written and some details may let us think they are somewhat unprofessional.
Accuracy and well-written emails share insights about the sender characteristic.
Would you ever reply to a marketing mail if it contains mistakes?
Probably not because, if the company would present the product with missing components or broken parts you would consider this as a poor-quality brand and eventually not buying from them.
This does not happen with phishing emails, which share this low accuracy and sophistication.
Whilst legitimate mail communications present a clear and neat structure, most frauds are characterized by the presence of words with grammar errors and misspellings.
What is the reason?
Although English as a language is simple and represents the most spoken language in the world, only 20% of the population is a native speaker.
This results in a nightmare for non-native people who have to learn and master this language in both spoken and written communication.
Nevertheless, only few proficient people can detect spelling errors, thus the rest is more prone to overlook such imprecisions because they are naïve.
Therefore, the question is why do they choose to write so badly if such communications only raise the attention of the most gullible people?
It is somehow a limitation to the effectiveness of the phishing campaign itself and bad actor should improve the quality of such mails.
This is intentional, because writing perfect emails can be counterproductive too.
Some bad actors deliberately use poor grammars and typos in order to get the attention of the victims.
Not all hackers use poor quality mails but they are aware that spam filters may detect scams.
Indeed, every mail provider implements an algorithm which is capable of detecting phishing emails and iteratively learn and detect such patterns.
If you receive so many emails from a specific sender or with a similar content, that mail would be put in the spam folder automatically by your email client.
Some email filters specifically look for exact matches of keywords which are relevant for scammers.
Therefore, if some words are misspelled they would not be detected by spam filters, thus reaching the inbox of the victims.
Email typos have also another great use case, which relates to human psychology.
Nowadays, gaining the attention of any type of audience is becoming more and more complicated, especially of the youngest people.
If an email contains misspelled word, it is easier for the victim to raise the attention and check the content.
Going through the content to check mistakes increase the chances of this mail being read.
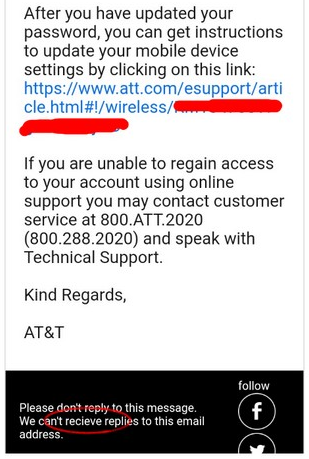
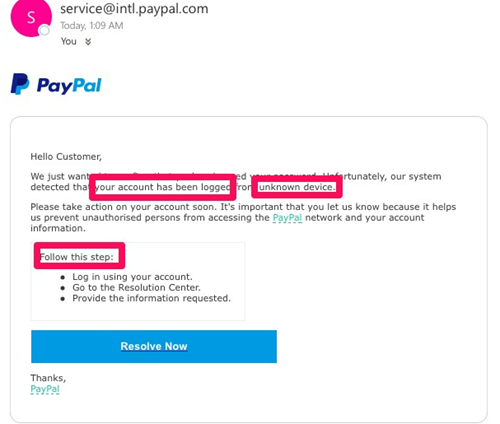
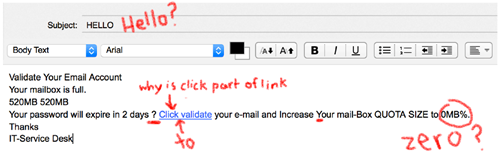
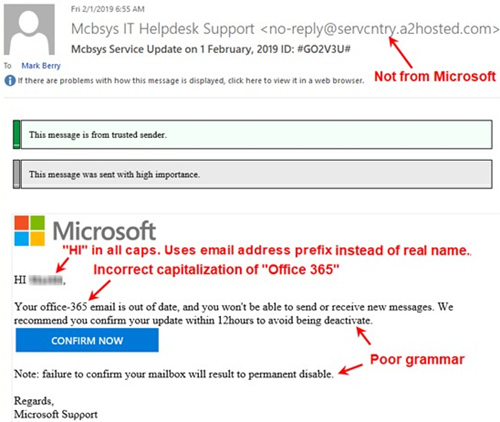
How does a poor quality scam email looks like?
Here's some examples
The information contained in this article is provided by White Blue Ocean, part of CRIF Group, a global company specializing in credit & business information systems, analytics, outsourcing and processing services, as well as advanced digital solutions for business development and open banking.
Reference List
https://www.egress.com/resources/cybersecurity-information/phishing/2021-phishing-statistics
https://medium.com/purple-theory/why-are-scam-emails-so-poorly-written-6fd186811401
https://umbrella.cisco.com/blog/grammar-and-spelling-errors-in-phishing-and-malware
https://www.ibm.com/downloads/cas/OJDVQGRY
https://www.proofpoint.com/it/threat-reference/phishing
The information contained in this article is provided for informational purposes only and does not constitute professional advice and is not guaranteed to be accurate, complete, reliable, current or error-free.

Related news

A Brief History of Ransomware
2023-11-10Ransomware is continuously developing and becoming more and more sophisticated. It isn’t going anywhere anytime soon, but where did it come from? Where did it go? And how has it evolved?
Read more
How to tidy up a data-irresponsible past
2022-04-11The world has never been more interconnected than at the present time, through devices like smartphones, laptops, and The risks of IoT devices, that create, collect, transmit, process, analyse, copy and store unprecedented amounts of data. This has led to concerns on how much control users have over their own data, and what level of privacy they can maintain when navigating online. Read more...
Read more
Hackers Are Using CAPTCHA as Attack Vector
2025-03-14Cybercriminals use malicious CHAPTCHAs to install stealers on victims' computers, collecting sensitive data such as emails, passwords, addresses, and financial information. We examine various attack methods, including watering hole attacks, ad abuse, and SEO poisoning, and provide practical tips for protecting yourself from these sophisticated threats.
Read more
New Mishing Campaigns Target Job Seekers
2025-01-31Mishing attacks, a form of mobile phishing, are being used in recruitment scams to target job seekers. These attacks involve sending fake job offers via SMS or messaging apps, leading victims to download malware onto their devices. This article explores the rise of mishing attacks, how they work, and the steps you can take to safeguard your personal information and financial data from these threats.
Read more
Italian convenience giant CONAD hit by Lynx ransomware
2025-02-07Italian retail chain CONAD was hit by the Lynx ransomware group on November 2024. Despite the breach, CONAD's immediate defensive measures successfully protected customer data. The article investigates on the tactics of Lynx, a Ransomware-As-A-Service group, and provides insights on how businesses can strengthen their cybersecurity defences.
Read more
Mind the Gap: Understanding Cybersecurity Gap Analysis
2025-01-10A cybersecurity gap analysis is a process used in organisations to evaluate the organization’s current defences, identifies vulnerabilities and weaknesses in the company security framework, and guides improvements, helping businesses prioritize risks and enhance defences. It’s an essential step in building a compliant security framework and staying ahead of evolving cyber threats.
Read more
The shift to private clouds: how cybercriminals are changing the monetization of stolen data
2024-11-22Subscription-based models in cybercrime allow hackers to offer stolen data in private clouds, reducing risks and boosting profits. For victims, this means greater threats as data becomes more accessible and exploitable over time.
Read more
Stealer Malware Logs
2024-04-05In recent months, stealer logs have emerged as a new threat spreading across dark web. Through an exploration of parsed and unparsed logs, this article unveils the motivations driving their widespread sharing and provides practicable steps to protect yourself from becoming a victim.
Read moreContacts
Let's talk
Please fill in the form below (fields with * are mandatory) and we will respond to your request as soon as possible!