How to tidy up a data-irresponsible past
2022-04-11
The world has never been more interconnected than at the present time, through devices like smartphones, laptops, and The risks of IoT devices, that create, collect, transmit, process, analyse, copy and store unprecedented amounts of data. This has led to concerns on how much control users have over their own data, and what level of privacy they can maintain when navigating online.
Internet Privacy
Internet privacy relates to users’ ability to control and consent to what information about themselves, their online activities and preferences is disclosed, tracked and used when they navigate the web.
Nowadays, there are numerous threats to users’ privacy online, be it by the hands of cybercriminals, businesses and third parties, governments, or users themselves. It is now well known that personal data is a valuable commodity to cybercriminals, who can use this to gain access to users’ online accounts, carry out phishing attacks and blackmail, commit identity theft, financial fraud, and much more. Cybercriminals are able to compromise users’ privacy by collecting information on them from social media platforms, carrying out attacks that lead to data breaches against businesses and organisations to access costumers’ data, and launching cyberattacks against users.
Threats to users’ privacy can also arise from online businesses and services, as many use cookies to track users’ online activity when visiting a website, including what they click on, which pages they visit, and their preferences. Online retailers and websites collect this information to perform user profiling and offer targeted advertisements, but can even use the information as an asset and sell it to third parties, when authorized.
Users’ own bad habits when navigating the web are one of the main threats to their own privacy.
Numerous users mindlessly give apps, website and services permission to access their camera, microphone, contact list, photo gallery and exact location. Typically, users also accept privacy, and terms and conditions policies, or the use of cookies on websites, without taking the time to read through the details. As reading these documents can be time-consuming to users, many are willing to simply accept them, and potentially compromise their privacy for the sake of convenience.
For scammers, there’s a lot to like about social media.
Users can also compromise their own privacy by oversharing on social media. According to experts, young internet users in particular tend to share more on social media both when it comes to their personal information, like their full name, city, school, date of birth, email address and phone number, and their feelings, thoughts and comments. Willingly disclosing this type and amount of information could potentially have long-term impacts for users when it comes to their future employability, their reputation, legal problems and threats like identity theft. In fact, by collating information taken from multiple social media platforms or websites, malicious actors can create an almost complete picture of a user.
According to US Federal Trade Commission, in 2021
- More than one in four people who reported losing money to fraud in 2021 said it started on social media with an ad, a post, or a message;
- 95,000 people reported about $770 million in losses (25% of all reported losses to fraud in 2021);
- people 18 to 39 were more than twice as likely as older adults to report losing money to these scams in 2021;
- more than half of people who reported losses to investment scams in 2021 said the scam started on social media;
- more than a third of people who said they lost money to an online romance scam in 2021 said it began on Facebook or Instagram;
- 45% of reports of money lost to social media scams in 2021 were about online shopping. In nearly 70% of these reports, people said they placed an order, usually after seeing an ad, but never got the merchandise.
US Federal Trade Commission stated that in 2021 total reported losses were about 18 times what they were in 2017, and the number of people who reported losing money in 2021 grew to 19 times higher than those reports in 2017.
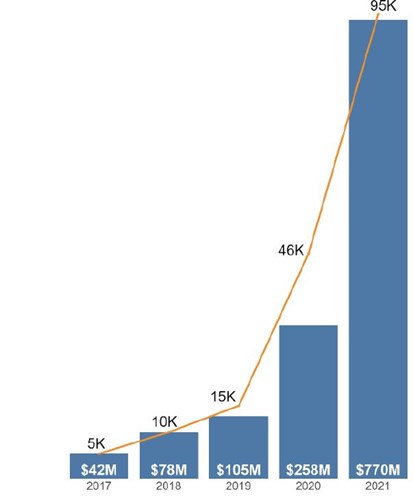
Figures based on fraud reports directly to the FTC indicating a monetary loss and identifying social media as the method of contact.
Social media a gold mine for scammers in 2021
Social media permeates the lives of many people – we use it to stay in touch, make new friends, shop, and have fun. But reports to the FTC show that social media is also increasingly where scammers go to con us. More than one in four people who reported losing money to fraud in 2021 said it started on social media with an ad, a post, or a message.1 In fact, the data suggest that social media was far more profitable to scammers in 2021 than any other method of reaching people.2
More than 95,000 people reported about $770 million in losses to fraud initiated on social media platforms in
2021.3 Those losses account for about 25% of all reported losses to fraud in 2021 and represent a stunning eighteenfold
Top frauds reported as originating on social media in 2021
While investment and romance scams topped the list on dollars lost, the largest number of reports came from people who said they were scammed trying to buy something they saw marketed on social media.
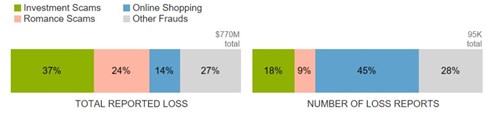
Figures based on fraud reports directly to the FTC identifying social media as the method of contact Investment scams include the following fraud subcategories: art, gems and rare coin investments, investment seminars and advice, stocks and commodity futures trading, and miscellaneous investments.
Whatever is shared on the web stays on the web.
Moreover, it is important to understand that whatever is shared on the web stays on the web. Even if it is possible for a user to ask a particular company for the removal of his/her private information, it is close to impossible to delete any appearance of that information from the web. Thus, users should be very careful about what they share and remember that data can reach the furthest corners of the internet whether they approve it or not.
Oversharing - tidying up the past and preparing for the future
There are ongoing debates on who should be responsible for ensuring users’ privacy, whether it should be organisations, the government, or individual users. While data privacy is not possible unless all three entities work towards the same goal, it is essential for users to become the first line of defense in protecting their own data. Throughout the past years, more and more users have admitted they worry about their privacy and about how their information is used. These same users however, then admitted to not having changed their online behaviour to address these concerns. Some users might think it is not worth trying to protect their privacy as a large amount of their information is already out there, but it is never too late to start tidying up the trail of information they have left behind.
How to protect accounts and devices
As more and more personal, financial and medical information is stored online it is essential to keep both devices and accounts secure. This can be done by using comprehensive anti-virus software and by keeping all devices up to date with the latest updates and security patches. Users should also protect their accounts by using strong unique passwords, and should avoid easy-to-guess passwords like first names, date of births, the name of their favourite sports team, or their favourite colour. It is recommended to use two-factor authentication for accounts where possible, to add an extra layer of protection.
Disable cookies and use a VPN
To protect their privacy when navigating the web, users are recommended to regularly clear or disable cookies, use ‘Incognito Mode’ which deletes cookies as soon as the browsing session is over, or use private search engines that do not track and log online activity. Users are also recommended to avoid using public Wi-Fi or use a personal VPN, as public Wi-Fi connections are typically not encrypted, and could allow malicious actors to monitor users' online activity.
Maximise privacy settings on social media platforms
Users should customise the privacy settings of their favourite social media sites to reach the level of privacy they desire. This can include limiting who can see what they share, who can look them up by using their email address, and who can tag them in content. Often these platforms have tools that allow users to check if anyone else is logged into their account, to make sure no one has gained unauthorised access. On platforms like Facebook, users can visit the ‘Apps and Websites’ area, where they can monitor which other services have access to the information they have used on Facebook.
Don’t overshare on social media platforms and delete old accounts
Users should also limit who they allow in their inner circle on social networks, and should carefully consider which information to share, and which to keep private instead. It is also always good practice to delete accounts that are no longer in use, rather than leaving them dormant, as these accounts typically have a wealth of personal information. This is will remove the risk that someone could hack into the dormant accounts and access personal information without users noticing, and will remove the risk of users’ data being compromised if the organisation suffers a data breach.
It is never too late for users to tidy up a past during which safeguarding their own privacy was not a main concern, and it is never too late for them to learn how to manage their information going forward. As the risk to users’ privacy will continue to grow in a world that is more and more connected through technological devices, users should remember that their own privacy starts from them.
The information contained in this article is provided by White Blue Ocean, part of CRIF Group, a global company specializing in credit & business information systems, analytics, outsourcing and processing services, as well as advanced digital solutions for business development and open banking.
Reference list:
https://www.bbc.co.uk/news/technology-41483723
https://www.cpomagazine.com/data-privacy/invasion-of-privacy-tracking-online-behavior-across-web/
https://news.mit.edu/2014/is-online-privacy-possible
https://www.theguardian.com/technology/2013/oct/21/teenagers-careless-about-online-privacy
https://techspirited.com/ethical-issues-of-internet-privacy
https://www.websafetytips.com/why-is-online-privacy-so-important/
https://www.ftc.gov/news-events/topics/protecting-consumer-privacy-security
The information contained in this article is provided for informational purposes only and does not constitute professional advice and is not guaranteed to be accurate, complete, reliable, current or error-free.

Related news

What Trump's Re-Election Means for US Data Privacy
2024-12-11Donald Trump’s re-election brings new debates about data privacy, AI regulation, and cybersecurity. This article evaluates his policies, from TikTok to encryption, and their possible effects on US citizens and innovation.
Read more
Dox Gangs Run Rampant, Victims Exposed for Life
2024-08-30Doxxing-as-a-Service (DaaS) is now a real and genuine threat that people need to be aware of, as it has become cheaper and simple to hire the service of a doxing group. DaaS enables identity fraud, spear phishing, malware deployment and even personal endangerment of its victims. In this article, we take a look at the types of DaaS services now on offer, and discuss ways that you may be able to protect yourself or mitigate the damage done by a dox.
Read more
A Brief History of Ransomware
2023-11-10Ransomware is continuously developing and becoming more and more sophisticated. It isn’t going anywhere anytime soon, but where did it come from? Where did it go? And how has it evolved?
Read more
Why phishing emails contain errors?
2022-05-04You have probably noticed that all the phishing mails are poorly written and some details may let us think they are somewhat unprofessional. Find out why.
Read more
Law Abiding Netizens: How Legislation Can Counter Cybercrime
2025-01-17Cybercrime threatens global economies, with losses expected to hit $10.5 trillion by 2025. This article explores how the EU leads the global fight against cybercrime threats through legislation like GDPR and DORA, setting global standards for data protection and cybersecurity.
Read more
Gazavat/Expiro Malware Spotted in Africa after Decade-Long Disappearance
2024-11-15Resurgent Expiro malware is spreading in Africa, leveraging advanced techniques to evade detection and steal sensitive data. Learn prevention and mitigation rules for consumers and business.
Read more
The risks of Internet of Things
2022-03-25The growing number of Internet of Things devices, set to reach 30 billion in 2025, offers many advantages, but also raises concerns over the possibility of cybersecurity risks. Read more about IoT vulnerabilities.
Read moreContacts
Let's talk
Please fill in the form below (fields with * are mandatory) and we will respond to your request as soon as possible!